I just had this error while trying to perform maven release:
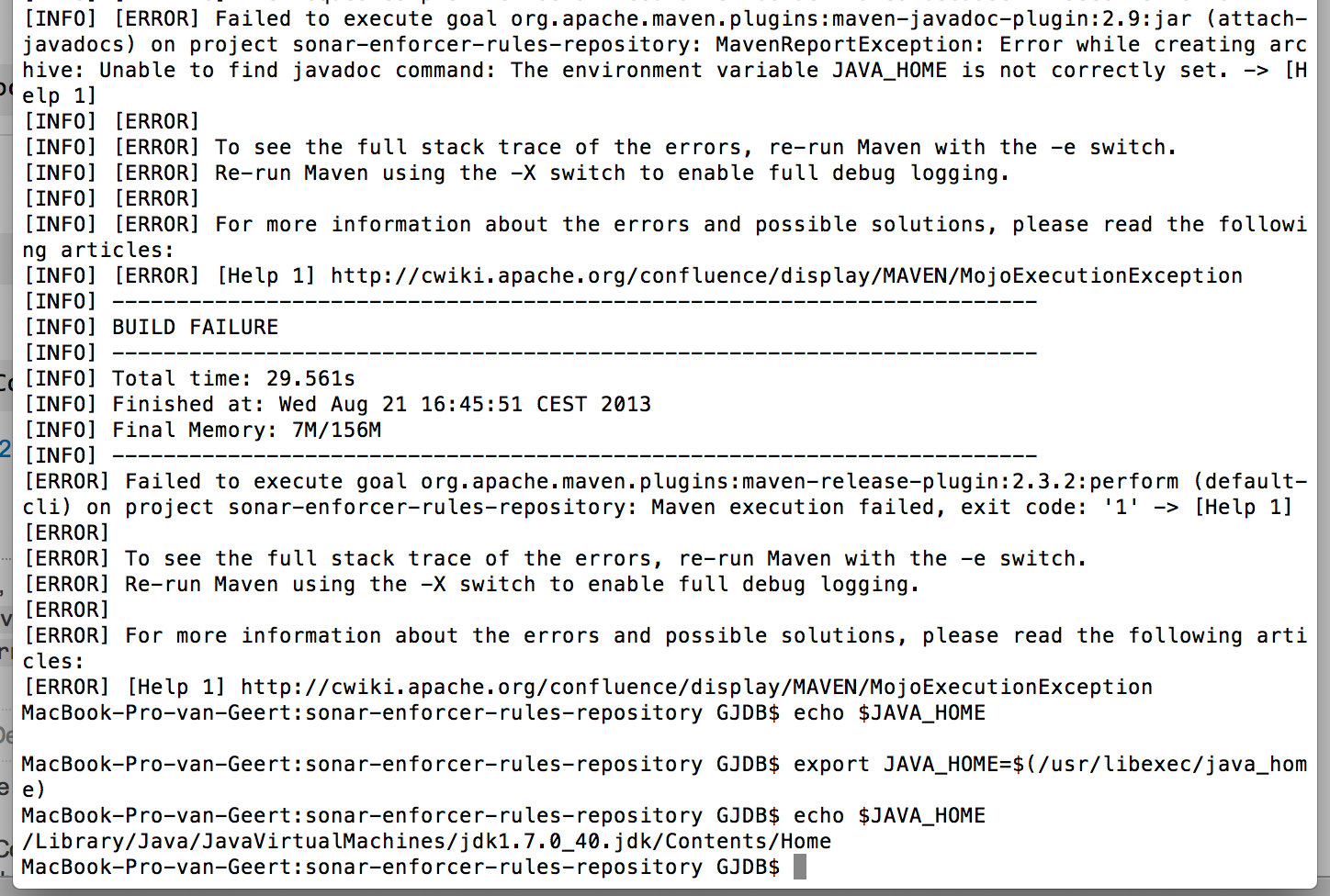
“[ERROR] Failed to execute goal org.apache.maven.plugins:maven-javadoc-plugin:2.9:jar (attach-javadocs) on project sonar-enforcer-rules-repository: MavenReportException: Error while creating archive: Unable to find javadoc command: The environment variable JAVA_HOME is not correctly set. -> [Help 1]”
How to fix? Simply:
1) Verify if the JAVA_HOME is really empty
MacBook-Pro-van-Geert:sonar-enforcer-rules-repository GJDB$ echo $JAVA_HOME
2) If empty: set it with the following command
MacBook-Pro-van-Geert:sonar-enforcer-rules-repository GJDB$ export JAVA_HOME=$(/usr/libexec/java_home)
3) Verify it has been set
MacBook-Pro-van-Geert:sonar-enforcer-rules-repository GJDB$ echo $JAVA_HOME
/Library/Java/JavaVirtualMachines/jdk1.7.0_40.jdk/Contents/Home